Public Key Infrastructure (PKI) has been around for a long time and I have been supporting PKI software from a pre-sale’s perspective for over 20 years. Many initial PKI initiatives over that time frame have mostly come out of the Department of Defense (DOD) and the Federal Government wanting to get rid of usernames and passwords to access resources – mission-critical ones at that.
They realized very quickly that the default Certificate Revocation List (CRL)-based solutions centered around smart-card login and website authentication were not the way to go. It takes up all the bandwidth just with users having to download CRLs that could be 20-30 MB each. Imagine thousands of users logging in to do their jobs at the same time on a Monday! All bandwidth would be utilized for downloading CRLs to validate user certificates have not been revoked and impacting the mission.
The Solution
This is where Axway Online Certificate Status Protocol (OCSP) came to the rescue and has been supporting DOD and Federal Civilian Agencies for many years to Validate user credentials on their Common Access Card (CAC) and Personal Identity Verification (PIV) smart cards for logging into their networks whether to a Domain or Web Site.
After DOD was successfully deploying CAC Smart Cards, the Government came out with HSPD-12 and Federal Agencies were supposed to set up a common credential across the Gov’t and DOD and this created the PIV specifications which are a standard for what must be on issued smart cards. If you are not familiar or want more details around the PIV specifications, PIV Usage Guides have good information on the standard.
Device Certificates: What does this have to do it?
I wanted to give a quick intro to PKI and smart cards as we now have a new use case that can also help other industries like finance, healthcare, supply chain and manufacturing.
Not much uptick has come out of PKI use cases other than the Federal Government and DOD when it comes to PKI and I believe a lot has to do with the complexity of deploying and the needed skilled IT folks to run and manage the solution in the past.
This is where a SaaS solution that issues and manages certificates and can also validate certificates in real-time to ensure they are still valid is a very viable solution. If properly managed, it can meet all security and federal regulations that these industries and devices require without extensive IT staff to manage, maintain, and support as it is included in a Managed SaaS solution if you go that route.
Device Certificates can be used to securely authenticate the device over its lifetime and ensure the identity of the device and the device owner. We are starting to see healthcare use cases where device certificates are being requested as well as automobile manufacturing using device certificates in cars and trucks.
What if the device is not that sensitive?
You may wonder about devices that may not need the protection of something that needs higher security like a nuclear missile for instance.
The way to provide different solutions for devices that need a higher level of assurance and security is to choose the appropriate PKI solution as there are differences in assurance levels and the terms used are normally High, Medium or Low.
The Certificate Authority vendor will typically have certificates to meet these requirements and a lot of the security is how the crypto keys are stored, accessed, managed and what type of Hardware Security Model (HSM) is used hardware FIPS 140-2 Level 3,4,5… or software only typically FIPS 140-2 Level 1 software only.
Why do you need one?
We have all seen the horror stories of what can happen to driverless cars if they are not secured. If you didn’t see it, in a nutshell, someone hacked and steered it off the road causing a crash. Or imagine having an Implantable cardioverter defibrillator (ICD) that if proper device certificate were not implanted with it someone could hack it and do not-so-good things. I would want a high-level assurance PKI Certificate on that device if implanted in me!
In closing this blog, I wanted to see what I could find regarding who is using Device Certificate in production. I found a program that the Department of Transportation is currently doing a pilot with device certificates in the Security Credential Management System that is using device certificates as explained above. Additional info on that can be found on the US Dot site.
More to come! There’s a lot of interest surrounding the topic. Researchers and use cases are requiring security that is easy to deploy and manage. Consumers and manufacturers can rely on more than no security that is typically the first to get thrown out into the wild.
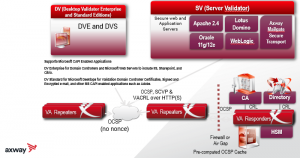
The following is Axway’s Validation Authority Suite Components and Basic Architecture that supports Validating Device Certificates to ensure they have not been revoked and can be very important in certain use cases as described in this blog.
Read more about HSPD 12, Axway Validation.

Follow us on social